
Case Studies
Case Study: Automating Social Media Content Creation with ChatGPT 4.0
Objective:
To create a streamlined system for generating engaging social media content for platforms like Instagram, Facebook, LinkedIn, Twitter, and TikTok. This system automates content ideation, creation, and optimization using ChatGPT 4.0 and AI-powered agents for analyzing viral trends.
Overview of the Automation System
Challenge:
Social media content creation is often tedious and requires constant adaptation to trends and audience preferences. Businesses need a solution to deliver high-quality, engaging posts that resonate with their target audience and save time.
Solution:
A system powered by ChatGPT 4.0 and AI agents that automates the following:
- 🌟 Generating content for Instagram, Facebook, LinkedIn, and Twitter in platform-specific formats.
- 🎥 Creating short-form scripts for TikTok and Instagram Reels.
- 📈 Tracking viral trends using AI agents to stay relevant.
- 🕒 Scheduling posts at optimal times for better engagement.
Content Creation Machine 🃏
Step-by-Step Implementation
1. Setting Up ChatGPT 4.0 for Content Generation
- Input Prompt Design: Develop specific prompts to instruct ChatGPT to create posts tailored to each platform.
- Example for Instagram: “Write a carousel post caption about [topic] with a call-to-action for engagement.”
- Example for TikTok: “Create a 15-second viral script about [topic] using humor.”
- Output Customization: Structure outputs to include hooks, body text, hashtags, and emojis for each platform.
2. Automating Viral Trend Analysis
- Use AI agents to scrape data from tools like BuzzSumo, TrendHunter, or Twitter Trending.
- Automate trend monitoring with Python scripts or Zapier integrations, feeding the most relevant data into ChatGPT for contextual content creation.
- Example: An agent tracks the top 10 viral hashtags in the fitness niche and feeds them to ChatGPT for integration into captions.
3. Streamlining Multi-Platform Content Distribution
- Batch Creation: Generate content for all platforms in a single session, ensuring coherence across posts.
- Formatting Adjustments: Tailor text lengths and tones for professional platforms like LinkedIn versus casual platforms like TikTok.
4. Generating Hooks and Scripts for Reels and TikToks
- Prompt ChatGPT to create attention-grabbing hooks:
- Example: “What if you could achieve X in just 5 minutes a day?”
- Generate short, punchy scripts designed for visual storytelling. Include suggestions for pacing and visuals.
5. Reviewing and Scheduling Content
- Use AI tools like Grammarly or Hemingway for polishing text before publishing.
- Automate scheduling with tools like Buffer, Hootsuite, or SocialBee to post at optimal times.
Results
- Time Saved: Reduced content creation time by 60%.
- Increased Engagement: Viral hooks and optimized captions resulted in a 30% increase in average engagement rates.
- Scalability: The system allowed consistent posting across four platforms without additional manual effort.
Key Takeaways
- Leveraging ChatGPT 4.0 enables quick generation of diverse, engaging social media content.
- AI agents enhance relevancy by identifying trending topics and patterns in real-time.
- This automated workflow is ideal for creators looking to maintain a consistent and impactful presence across multiple platforms.
Tools Used:
- ChatGPT 4.0: For content generation and scriptwriting.
- BuzzSumo and TrendHunter: For identifying viral topics and trends.
- Hootsuite/Buffer: For scheduling and publishing.
This case study highlights the effectiveness of AI-driven systems in transforming social media strategies, making it easier for businesses and creators to thrive in the digital space.
You said:
use professional looking emoji
ChatGPT said:
Case Study: Automating Social Media Content Creation with ChatGPT 4.0
Objective:
To develop a professional and automated system for creating engaging social media content tailored for Instagram, Facebook, LinkedIn, Twitter, and TikTok. This automation ensures viral hooks, optimized captions, and consistent posting across platforms with minimal manual effort.
Overview of the Automation System
Challenge:
Social media content creation is often tedious and requires constant adaptation to trends and audience preferences. Businesses need a solution to deliver high-quality, engaging posts that resonate with their target audience and save time.
Solution:
A system powered by ChatGPT 4.0 and AI agents that automates the following:
- 🌟 Generating content for Instagram, Facebook, LinkedIn, and Twitter in platform-specific formats.
- 🎥 Creating short-form scripts for TikTok and Instagram Reels.
- 📈 Tracking viral trends using AI agents to stay relevant.
- 🕒 Scheduling posts at optimal times for better engagement.
Step-by-Step Implementation
1. Setting Up ChatGPT 4.0 for Content Generation
- 🖋️ Custom Prompts: Develop detailed prompts for ChatGPT to generate content tailored to specific platforms.
- Example for Instagram: “Write a carousel post caption for [topic] with emojis and a strong CTA.”
- Example for LinkedIn: “Create a professional LinkedIn post for [topic] with a focus on thought leadership.”
- 🎯 Keyword Optimization: Integrate trending keywords and hashtags for each platform to boost visibility.
2. Automating Viral Trend Analysis
- 🔍 AI Trend Agents: Use tools like BuzzSumo or Twitter API to monitor viral content in your niche.
- 🤖 Data Automation: Feed real-time trending topics and hashtags directly into ChatGPT for dynamic content creation.
- Example: An AI agent scrapes the top hashtags in the fitness industry and suggests: #FitLife #MotivationMonday.
3. Multi-Platform Content Distribution
- 📤 Batch Content Creation: Use ChatGPT to generate posts for all platforms at once, adapting tone and length for each.
- ✂️ Formatting Adjustments: Optimize captions for Twitter’s character limits and LinkedIn’s professional tone.
4. Crafting Viral Hooks and Scripts for TikTok & Reels
- 🚀 Viral Hooks:
- Example: “What if I told you [X solution] could save you 10 hours a week?”
- 🎬 Short Scripts: Use ChatGPT to create concise and engaging scripts that align with visual storytelling.
5. Scheduling and Review Process
- 📆 Automation Tools: Integrate with Hootsuite or Buffer for seamless scheduling.
- ✅ Quality Assurance: Use Grammarly or Hemingway to refine language and ensure professional tone.
Results Achieved
- ⏳ Time Efficiency: Reduced content creation time by 60%.
- 🚀 Improved Engagement: Viral hooks and trend-driven captions boosted average engagement rates by 35%.
- 📊 Scalability: Enabled consistent, high-quality content delivery across multiple platforms.
Key Benefits of the System
- 🌐 Centralized content creation and management.
- 🔥 Trend-driven posts to maximize visibility.
- 🤝 Better alignment with audience preferences through platform-specific formats.
Tools Used
- 🧠 ChatGPT 4.0: For generating content and scripts.
- 📊 BuzzSumo: For analyzing viral trends.
- 📅 Hootsuite/Buffer: For scheduling and posting.
This automated system for social media content creation ensures efficiency and consistency, empowering businesses to thrive in the competitive digital landscape. With ChatGPT 4.0, creators can focus on strategy while AI handles the heavy lifting! 💼✨

Article
In conversations with operations, IT and architecture leaders, one question comes up most frequently: “What makes a SOAP different from our scheduler or iPaaS — and why should we invest now?”
It’s a fair question. And the answer isn’t just focused on why you should add another automation tool. Instead, considering a Service Orchestration and Automation Platform (SOAP) means you’re ready to think about the operational model behind how work moves across your organization.
A scheduler triggers tasks, an iPaaS connects applications, but a modern SOAP coordinates end-to-end business processes across systems, teams and environments in a way that maintains reliability at enterprise scale. That difference shows up directly in operational resilience, business agility and cost control.
The 2025 Gartner® Critical Capabilities for SOAP report is the clearest framework I’ve seen for tying platform strengths to financial outcomes. Here’s how I help leaders like you use that framework to build a credible business case.
The framework: Mapping Use Cases to your P&L
The Critical Capabilities report doesn’t start with architecture diagrams or methodology. It starts with how platforms perform against five operational Use Cases, each representing a measurable part of your business. I find these especially useful because they line up almost perfectly with the major categories of cost, risk and productivity that executives care about:
- Operational resilience
- Business agility
- Cost optimization
- Risk management
- Speed to insight
Instead of thinking of them as technical buckets, think of them as the five pillars that determine whether your automation investments actually return value. A SOAP that scores well across all five transforms automation from a technical initiative into an engine for enterprise performance.
Pillar 1: IT workload automation and the ROI of unbreakable operations
The business challenge:
A pervasive pattern I see is IT teams stuck in a reactive mode. Excessive time is spent on firefighting and manual monitoring, which draws focus away from strategic process improvement. This reactive posture results in costly consequences, including missed service-level agreements (SLAs), silent failures in critical overnight processes and a constant backlog of expensive incidents.
What this Use Case measures:
Gartner considers this the foundation of SOAPs: Can the platform run critical workloads reliably across hybrid and multi-cloud environments? Think financial close, inventory syncs, regulatory reporting — with real-time awareness and automated recovery. This means it must offer dependency management that understands system context, recovery paths that prevent cascading failures and observability that lets operators diagnose and resolve issues quickly.
Where the ROI shows up:
- Reduced downtime costs: Preventing failures before they hit the business
- Lower operational overhead: Fewer hours spent monitoring or intervening
- Strategic consolidation: Eliminating multiple schedulers, licenses and skillsets
This is the first place most organizations find real cost savings, because reliability is expensive when you’re compensating for it manually.
Pillar 2: IT workflow orchestration and the value of cross-team agility
The business challenge:
Most delays don’t come from individual tasks. They come from the handoffs: the approvals that get stuck in someone’s inbox, the data that wasn’t validated, the system that didn’t trigger the next step. Teams often automate inside their own domains but leave the gaps between them unmanaged.
What this Use Case measures:
Gartner looks at how well a SOAP can coordinate entire processes, not just tasks:
- Cross-application workflows (ERP + ITSM + SaaS + custom apps)
- Conditional logic and exception handling
- Orchestration spanning on-premises and cloud environments
Where organizations see ROI:
- Shorter cycle times: End-to-end processes move without waiting on human intervention
- Higher throughput: Fewer restarts, errors or duplicate work
- Greater adaptability: Workflows that adjust as business requirements change
The payoff is simple: people get hours back. Not to mention, change doesn’t feel risky anymore.
Pillar 3: Data orchestration and the payoff of faster, smarter decisions
The business challenge:
Analytics teams can only move as fast as the data feeding them. Many organizations are still juggling multiple disjointed ETL solutions, insecure file transfers or inconsistent handoffs between systems. The result is predictable: delays, inconsistent data and missed windows for decision-making.
What this Use Case measures:
Gartner evaluates a SOAP’s ability to orchestrate reliable, governed data pipelines:
- Event-driven movement from systems like SAP to data warehouses like Snowflake
- Managed file transfers with dependency tracking
- Data validation, reconciliation and exception handling
- Automated triggers to BI, AI or other downstream applications
Where organizations see ROI:
- Faster time-to-insight: Data arrives validated and on time
- Improved compliance: Centralized audit trails remove the risks of custom scripts with no single source of truth
- Eliminated bottlenecks: Analytics teams spend less time waiting and more time analyzing
This is where organizations often unlock value they didn’t realize they were losing.
Pillar 4: Citizen automation and the advantage of empowered teams
The business challenge:
IT teams become bottlenecks when every routine request — from report generation to onboarding steps — has to be manually actioned. The backlog grows and the business slows.
Yet handing automation directly to business users without governance isn’t an option.
What this Use Case measures:
Gartner evaluates this capability by looking at how well a platform can distribute automation safely without losing control. It’s essentially a test of whether your Operations team can create guardrails that let business users trigger approved workflows on demand without introducing risk. A strong score here reflects a platform that supports low-code execution, reusable templates and full auditability, so non-technical users can initiate routine actions while IT retains oversight. This Use Case ultimately measures how effectively a SOAP can push automation closer to the edge of the business without allowing fragmentation or shadow IT to creep back in.
Where organizations see ROI:
- Faster turnaround: Teams get what they need without waiting days or weeks
- Reduced IT ticket volume: Freeing technical staff to focus on higher-value work
- Fewer errors: Standardized workflows eliminate risky and error-prone manual steps
When done right, citizen automation is not “shadow IT.” It’s a controlled extension of enterprise automation.
Pillar 5: DevOps automation and the competitive edge of continuous delivery
The business challenge:
Software teams often automate their CI/CD pipelines but leave the surrounding processes — environment provisioning, test data setup, dependency coordination — untouched. Those manual steps are what slow releases and introduce inconsistencies.
What this Use Case measures:
For DevOps automation, Gartner focuses on how deeply the platform can integrate into modern delivery pipelines and how reliably it can coordinate the steps surrounding deployment. It’s about assessing whether automation can move at the same pace as engineering, from provisioning and testing to promotion and release. High-performing platforms demonstrate support for automation-as-code practices, event-based triggers and consistent orchestration across environments. Use these parameters to gauge a provider’s ability to remove bottlenecks from the software lifecycle so teams can deliver changes quickly without compromising reliability or governance.
Where organizations see ROI:
- Shorter release cycles: Faster, safer path from commit to production
- Higher developer productivity: Fewer manual tasks around the deployment lifecycle
- More reliable deployments: Consistency enforced across environments
This is increasingly a strategic differentiator for teams moving toward cloud-native delivery models.
An undeniable case for a strategic investment
A scheduler reduces manual effort, whereas a SOAP reduces friction across your entire operating model. When a single platform delivers across all five Gartner Use Cases, you’re not just buying automation capabilities — you’re buying:
- Fewer outages
- Faster decisions
- Higher team velocity
- Lower integration costs
- Stronger risk posture
- A future-proof automation foundation
This is the business case every CFO wants: clear outcomes tied to operational, financial and strategic value. The next time you evaluate platforms, don’t ask, “What does it automate?” Ask, “Where does it impact my P&L?”
That’s the difference between a tool and a transformation partner.
Evaluate SOAP vendors with our scorecard, and download the full Gartner Critical Capabilities report to compare how leading platforms perform against these five essential Use Cases.

Uncategorized
With its latest release, AppViewX delivers new CLM and quantum-safe innovations to help organizations strengthen security, reduce compliance gaps, and maximize time to value
NEW YORK, Dec. 03, 2025 (GLOBE NEWSWIRE) — AppViewX, the leader in automated Certificate Lifecycle Management (CLM) and Public Key Infrastructure (PKI) software, today announced significant enhancements to its AVX ONE Platform, enabling enterprises to meet the upcoming 47-day SSL/TLS certificate validity mandate with speed and confidence. The release also introduces new automation and quantum-safe capabilities that simplify compliance, improve security posture, and deliver measurable ROI.
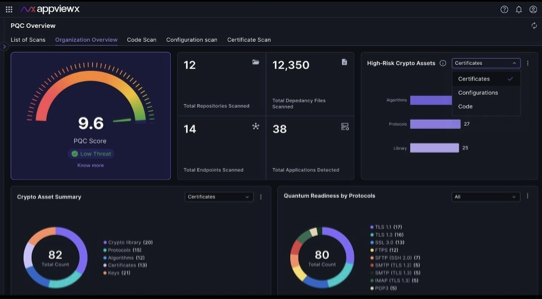
As certificate lifespans shrink rapidly over the next few years, the result will be surging renewal volumes, which will lead to significant operational and compliance risks for organizations. The AVX ONE platform eliminates these challenges by automating certificate discovery, provisioning, renewal, and revocation, ensuring continuous compliance with crypto-agility across hybrid and multi-cloud environments.
“Our customers need a future-proof solution that transforms regulatory pressure into operational excellence,” said Paul Trulove, Chief Product Officer at AppViewX. “This release underscores our commitment to rapid time-to-value, measurable ROI, and innovation that helps enterprises succeed in the age of 47-day certificates and a post quantum computing world.”
AppViewX Product Release Highlights
Manage Short-Lived Certificates at Scale
Automate renewal cycles and enforce re-enrollment policies to meet 47-day mandates without added overhead. Gain flexible control over certificate lifespans, automatically generate new private keys for improved security and leverage enhanced reporting for continuous compliance.
Advance Crypto-Agility and PQC Readiness
Demonstrate leadership in post-quantum preparedness with a comprehensive list of cryptographic assessments and remediation. AppViewX generates a Cryptographic Bill of Materials (CBOM) across certificates, algorithms, libraries, and applications, with clear remediation recommendations and a unified dashboard for executive reporting.
Gain Actionable AI Insights
Use natural-language search and AI-driven dashboards to get instant visibility into certificate operations with no scripts or technical queries required. AI-enabled navigation makes complex tasks effortless (such as “rotate a certificate,” “add a device group”, etc.) and saves time.
Accelerate Time-to-Value and ROI
Use predefined policy templates and out-of-the-box onboarding to dramatically reduce setup time. Enterprises can deploy in days, standardize compliance, and prove ROI faster, turning regulatory pressure into a business advantage.
Driving ROI in the Age of 47-Day Certificates
With its latest release, AppViewX ensures enterprises can:
- Improve certificate lifecycle automation with key enhancements to meet CA/B Forums new 47-day mandate
- Reduce operational costs, improve user experience and accelerate time to value.
- Demonstrate leadership in PQC readiness.
- Empower teams with AI-driven visibility and insights.
Availability
The November 2025 Product Release is available immediately from AppViewX. For details, read here.
See Innovation in Action: Gartner IAM
AppViewX will showcase its latest CLM and PQC innovations at the 2025 Gartner Identity & Access Management Summit in Dallas, December 8–10 (Booth #227). To see a demo or reserve your seat for our VIP dinner, register here.
As PQC timelines accelerate, organizations must begin foundational steps, starting with visibility and inventory, as early as next year. According to Gartner®, “No later than mid-2026, build and maintain a complete inventory of cryptographic assets to inform postquantum cryptography (PQC) migration planning.”¹
1Gartner, “Post-Quantum Cryptography: Why You Need to Be Ready by 2030” by Mark Horvath and Sarah Almond, October 27, 2025.
Gartner is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission.

Uncategorized
Key Takeaways
- TLS certificates shrink from 398 days to 47 days by March 15, 2029, requiring 7,766 annual renewals per 1,000 certificates
- CA/Browser Forum Ballot SC-081v3 passed with 29 votes in favor, zero opposed, signaling unanimous industry alignment
- Three-phase implementation: 200 days (March 2026), 100 days (March 2027), 47 days (March 2029)
- Organizations implementing automation now gain 2-3 year advantage in operational excellence and cost efficiency
- Domain validation reuse drops to 10 days by March 2028, requiring weekly revalidation cycles
- Crypto-agility becomes essential for preparing for post-quantum cryptography transitions by 2035
The cybersecurity landscape is undergoing its most significant transformation in the history of certificate management. When the CA/Browser Forum approved Ballot SC-081v3 in April 2025, it set in motion a fundamental shift that will redefine how organizations approach digital trust. This comprehensive guide examines the 47-day certificate mandate, its timeline, industry impact, and implications for your organization’s security posture.
What Are 47-Day Certificates?
The Fundamental Change
A 47-day certificate represents the new maximum validity period for publicly trusted TLS certificates, effective March 15, 2029. This dramatic reduction fundamentally alters the operational dynamics of certificate lifecycle management. Where organizations currently renew certificates roughly once per year, the 47-day model requires renewal every six to seven weeks, a ninefold increase in renewal frequency.
The change extends beyond simple validity reduction. Domain control validation, currently reusable for up to 398 days, will shrink to just 10 days by March 2028. This means organizations must prove domain ownership roughly every week and a half, adding another layer of operational complexity to certificate lifecycle management.
Historical Context of Certificate Validity Periods
Understanding the 47-day mandate requires examining the evolution of certificate lifespans:
- Pre-2011: Certificates valid for 5+ years were common
- 2012-2015: Industry moved to a 3-year maximum
- 2015-2018: Reduced to 2-year maximum (825 days)
- 2018-2020: Further reduced to 1 year + renewal buffer (398 days)
- 2020-present: Current 398-day maximum
- 2026-2029: Phased reduction to 47 days
Each reduction has strengthened security while increasing operational overhead. The certificate authority market’s growth from $173.1 million in 2023 to a projected $401.4 million by 2030 reflects the rapidly growing demand for digital certificates. As certificate volumes surge, manual processes cannot scale, especially with shorter validity periods.
The Complete Timeline: From 398 to 47 Days
Table 1: Certificate Validity Reduction Timeline
| Phase |
Effective Date |
Maximum Validity |
Annual Renewals (per 1,000 certs) |
Daily Operations |
Key Changes |
| Current |
Present |
398 days |
917 |
2.5 |
Baseline |
| Phase 1 |
March 15, 2026 |
200 days |
1,825 |
5 |
First major reduction |
| Phase 2 |
March 15, 2027 |
100 days |
3,650 |
10 |
Acceleration phase |
| Phase 3 |
March 15, 2029 |
47 days |
7,766 |
21.3 |
Final implementation |
Source: CA/Browser Forum Ballot SC-081v3

Phase-by-Phase Breakdown
Phase 1: March 15, 2026 – The 200-Day Transition
The first reduction to 200 days (180 days plus a 20-day renewal window) represents a 50% decrease from the current validity. Organizations will experience:
- Doubling of renewal frequency from annual to semi-annual
- Initial stress testing of automation capabilities
- Identification of process bottlenecks
- First wave of forced modernization for legacy systems
The phased reduction aims to make the proposed changes “reasonable and attainable”, giving organizations time to adapt their infrastructure and processes. According to Gartner’s 2024 research on PKI challenges, PKI has become a bigger challenge for organizations than multi-factor authentication, with certificate lifecycle management complexity cited as a primary concern.
Phase 2: March 15, 2027 – The 100-Day Acceleration
The 100-day validity period marks the acceleration phase, where manual management begins breaking down:
- Certificates require renewal every three months
- Organizations face 10 daily operations for 1,000 certificates
- Manual tracking in spreadsheets becomes error-prone
- This phase triggers widespread automation adoption as organizations recognize that manual processes cannot scale
Learn more about essential automation protocols like ACME that enable this transition.
Phase 3: March 15, 2029 – The 47-Day Reality
The final 47-day maximum represents the end state where:
- Certificates expire every 6-7 weeks
- 21 daily renewal operations become the norm
- Domain revalidation occurs weekly
- Manual management becomes mathematically impossible
- Only automated systems can maintain compliance

Why Is the Industry Making This Change
Security Benefits of Shorter Lifespans
The CA/Browser Forum’s rationale for shorter certificates centers on three critical security improvements:
- Reduced exposure window: Compromised certificates remain valid for shorter periods
- Faster algorithm transitions: Deprecated cryptography phases out quickly
- Improved validation accuracy: Domain ownership verified more frequently
Shorter certificate lifecycles represent a fundamental shift in how the industry approaches digital trust and security resilience.
Addressing Modern Threat Vectors
Contemporary cybersecurity challenges demand shorter certificate lifecycles:
- Supply chain attacks: Compromised certificates in third-party integrations
- Insider threats: Reduced window for malicious certificate usage
- Cryptographic vulnerabilities: Faster response to algorithm weaknesses
- Compliance requirements: Meeting evolving regulatory standards like NIST, PCI, DORA etc
NIST emphasizes shorter validity periods as essential for maintaining security in rapidly evolving threat landscapes, particularly as organizations prepare for the post-quantum cryptography transition.
Browser Vendor Perspectives
Browser vendors unanimously support the change, viewing it as essential infrastructure modernization:
- Google Chrome (73% desktop browser market share) states that it provides enhanced protection through frequent validation, reduces the window of vulnerability for 3+ billion users
- Apple Safari believes it will improve ecosystem security across iOS, iPadOS, and macOS devices
- Mozilla Firefox thinks it brings alignment with modern web security standards and open web principles
- Microsoft Edge states it reduces the attack surface for enterprise environments and cloud services
The official voting record shows 29 votes in favor, zero opposed, unprecedented consensus in CA/Browser Forum history, demonstrating industry-wide commitment to this security evolution.
Impact Analysis: What This Means for Organizations
Timeline Compression Impact
When certificate validity drops to 47 days, organizations managing 1,000 certificates will execute 7,766 renewal operations annually. That’s 21 operations every single working day (calculated from CA/Browser Forum Ballot SC-081v3 requirements).
Federal agencies alone face a $7.1 billion migration cost to post-quantum cryptography by 2035, per White House Office of Management and Budget estimates, with NIST’s timeline mandating deprecation of RSA and ECDSA by 2030.
Organizations implementing automation achieve dramatic time savings, ranging from hours to minutes, in certificate management time, and completely eliminate certificate-related outages, resulting in millions of dollars in saved costs and protected revenue.
Explore our comprehensive guide on choosing the right certificate lifecycle management solution.
Table 2: Certificate Lifecycle Evolution – Manual vs. Automated Operations – 1000 certificates portfolio
| Metric |
Current State (398 days) |
2026 (200 days) |
2027 (100 days) |
2029 (47 days) |
With Automation |
| Annual Renewals (1,000 certs) |
917 |
1,825 |
3,650 |
7,766 |
7,766 (automated) |
| Daily Operations Required |
2.5 |
5 |
10 |
21.3 |
21.3 (automated) |
| FTE Hours Required Annually* |
2,751 (minimum) |
5,475 (minimum) |
10,950 (minimum) |
23,298 (minimum) |
500-750** |
| Average Time per Renewal |
3-4 hours |
3-4 hours |
3-4 hours |
3-4 hours |
<5 minutes*** |
| Compliance Audit Prep Time**** |
3-5 days |
5-7 days |
7-10 days |
10-15 days |
2-4 hours |
| Deployment Method |
Manual |
Manual |
Manual |
Manual |
API/Automated |
Source: Calculations based on CA/Browser Forum Ballot SC-081v3 timeline, assuming 3 hours average manual processing time per certificate and industry standard error rates from IETF RFC 8555
*Assumes standard renewals without complications. Complex deployments, failed validations, or emergency revocations require additional time and attention.
**The automation estimate includes monitoring, exception handling, and periodic system maintenance. Actual hours depend on automation maturity and infrastructure complexity
***ACME protocol challenges complete in under 15 seconds, with total renewal typically under 30 seconds including network latency. <5 minutes is a safe estimate.
****Audit preparation times are industry estimates and vary by organization size and compliance requirements.

Operational Impact by Organization Size
Table 3: 47-Day Certificate Impact by Organization Size
| Organization Size |
Certificate Count |
Daily Operations at 47 Days |
Annual FTE Hours* |
Automation Requirement |
| Small Business |
10-50 |
0.2-1 |
233-1,165 |
Recommended |
| Mid-Market |
100-500 |
2-11 |
2,330-11,649 |
Essential |
| Enterprise |
1,000-5,000 |
21-106 |
23,298-116,490 |
Critical |
| Global Enterprise |
10,000+ |
213+ |
232,980+ |
Mandatory |
*Based on industry estimates of 3 hours per manual certificate renewal and installation

Transforming Certificate Management into Competitive Advantage
Strategic Benefits of Early Adoption
Organizations that implement certificate lifecycle automation now transform this mandate from a compliance burden into a strategic enabler:
Operational Excellence:
- Eliminate manual renewal bottlenecks
- Reduce human error and misconfigurations
- Enable self-service certificate requests for development teams
- Free security teams to focus on strategic initiatives
Business Agility:
- Accelerate application deployment cycles
- Support rapid scaling for new services
- Enable seamless multi-cloud operations
- Reduce time-to-market for digital initiatives
Security Posture:
- Achieve complete certificate visibility across environments
- Enforce consistent security policies
- Enable rapid response to vulnerabilities
- Build a foundation for crypto-agility
Competitive Positioning:
- Demonstrate security maturity to customers and partners
- Meet stringent compliance requirements effortlessly
- Support modern DevOps and cloud-native architectures
- Position for future cryptographic transitions
Read about the seven stages of certificate management to understand the full lifecycle.
The Window of Opportunity
Organizations fall into three categories based on their preparation timeline:
Early Adopters (2024-2026):
- Smooth transition through all phases
- Time to refine processes and build expertise
- Competitive cost advantages through gradual implementation
- Enhanced security posture as a differentiator
- Complete preparation for the 2029 deadline
Pragmatic Majority (2026-2027):
- Adequate preparation time for Phases 1 and 2
- More compressed timeline for final transition
- Standard implementation approach
- Achievable but requires focus and resources
Late Adopters (2028-2029):
- Crisis-mode implementation
- Higher costs due to rushed deployment
- Limited optimization opportunities
- Operational disruption during transition
- Competitive disadvantage
The choice of timing directly impacts not only implementation success but also long-term operational efficiency and strategic positioning.
Take Action Now: Schedule a personalized demo to see how AppViewX can prepare your organization for the 47-day transition before Phase 1 begins in March 2026.
Future-Proofing Your Certificate Infrastructure
Prepare for Accelerating Change
- By 2030, quantum-vulnerable algorithms like RSA and ECDSA will be deprecated, and by 2035, they’ll be entirely disallowed per NIST’s post-quantum timeline
- Certificate validation data reuse periods continue shrinking
- New compliance requirements emerge regularly, including DORA and updated PCI DSS standards
Build Organizational Capabilities
- Develop internal expertise in certificate lifecycle management
- Establish partnerships with certificate automation providers
- Create documentation and training programs
- Assign clear responsibility for certificate management across teams
Measure and Optimize
Track key metrics:
- Mean time to certificate deployment
- Certificate-related incident frequency
- Compliance audit performance
- Automation coverage percentage
Learn about 10 best practices for continuous compliance when managing digital certificates.
Essential Capabilities for 47-Day Success
Effective automation platforms must provide comprehensive capabilities to handle the 47-day lifecycle. According to Gartner’s 2025 Buyers’ Guide for PKI and Certificate Lifecycle Management, organizations should prioritize:
- Automated discovery to maintain certificate visibility across hybrid and multi-cloud environments
- ACME protocol support for automated certificate issuance and renewal
- Policy enforcement to ensure compliance with organizational security standards
- Integration capabilities with existing infrastructure, CAs, and DevOps tools
- Monitoring and alerting for exception handling and proactive management
- Self-service workflows enabling developers while maintaining security controls
AVX ONE CLM provides these capabilities through a unified platform approach, enabling organizations to scale certificate operations without proportionally scaling team size. Recognized by Gartner’s for effectively managing organization’s certificates, AppViewX delivers enterprise-grade automation with proven results.
Building Crypto-Agility for the Future
Preparing for Post-Quantum Cryptography
The 47-day mandate prepares organizations for larger cryptographic transitions ahead:
NIST’s post-quantum cryptography timeline targets widespread adoption by 2035, requiring organizations to:
- Replace current cryptographic algorithms with quantum-resistant alternatives
- Support hybrid certificate approaches during transition periods
- Maintain backward compatibility while enhancing security
- Manage algorithm agility across diverse systems
Organizations with mature certificate automation can:
- Transition algorithms in weeks versus years for manual processes
- Test new cryptographic approaches without production risk
- Roll back quickly if issues emerge
- Maintain complete visibility during transitions
AppViewX PKI-as-a-Service positions organizations for post-quantum readiness while addressing today’s 47-day certificate requirements.
The Path to Crypto-Agility
Near-term (2025-2029):
- Master 47-day certificate lifecycle automation
- Build organizational muscle for rapid certificate operations
- Establish discovery and inventory practices
- Develop policy frameworks for cryptographic standards
Mid-term (2030-2033):
- Begin post-quantum cryptography testing
- Implement hybrid certificate support
- Update systems for algorithm agility
- Train teams on new cryptographic standards
Long-term (2034-2035+):
- Complete post-quantum transition
- Maintain crypto-agility for future algorithms
- Continuous cryptographic risk assessment
- Proactive adoption of emerging standards
Organizations that view 47-day certificates as an isolated compliance requirement miss the larger strategic opportunity. Those that build true crypto-agility gain a lasting competitive advantage.
Explore what the table stakes are for certificate lifecycle management in 2026 and beyond.
Take Your Next Step Toward 47-Day Certificate Readiness.
The transition to 47-day certificates is inevitable. The question isn’t whether to automate, but when and how. Organizations that act now will lead their industries in security posture, operational efficiency, and crypto-agility.
Choose Your Path Forward:
Schedule a Live Demo → See AppViewX in action with a personalized demonstration tailored to your environment
Download the Gartner Buyers’ Guide → Get expert guidance on evaluating PKI and CLM solutions
Contact Our Team → Discuss your specific requirements with our PKI experts

Uncategorized
Key Takeaways
- Automation reduces certificate management time by 73-82%, transforming 23,298 annual hours to just 500-750 hours for 1,000 certificates.
- Organizations face an average of 4 certificate-related outages over 2 years, with each incident costing $11.1 million per outage event
- ACME protocol enables automated certificate renewal with validation typically completed in seconds, compared to hours or days for manual processes
- Organizations typically discover 5-10 times more certificates than expected during automated discovery processes
- Implementation requires three phases: Discovery (2-4 weeks), Automation Deployment (6-8 weeks), and Enterprise Scale (3-6 months)
As TLS certificate validity periods compress from 398 days today to just 47 days by 2029, manual certificate management becomes increasingly challenging, ultimately transforming into a mathematically impossible task. Organizations managing a 1,000-certificate portfolio will require 21 certificate operations daily, excluding weekends and holidays. This technical guide provides a comprehensive blueprint for implementing certificate lifecycle automation, delivering measurable ROI while preparing your infrastructure for the future of digital identity management.
Understanding Certificate Lifecycle Automation
What Is Certificate Lifecycle Automation?
Certificate lifecycle automation encompasses the end-to-end orchestration of TLS certificate operations through programmatic workflows, eliminating the need for manual intervention. Unlike traditional approaches requiring human operators to track expiration dates, generate certificate signing requests (CSRs), and install certificates, automated systems handle the entire lifecycle, from initial provisioning through renewal and eventual decommissioning, without human touchpoints for standard operations.
Modern certificate lifecycle automation platforms such as AVX ONE integrate directly with certificate authorities (CAs), infrastructure components, and security tools to create a self-healing ecosystem. When a certificate approaches expiration, the system automatically initiates renewal, validates domain control, obtains the new certificate, deploys it across all endpoints, and verifies successful installation, all while maintaining comprehensive audit trails.
The Business Case for Automation
The certificate authority market’s growth from $173.1 million in 2023 to a projected $401.4 million by 2030 reflects the rapidly increasing demand for digital certificates. As certificate volumes surge, manual processes cannot scale. With 71% of IT professionals admitting they don’t know their actual certificate count, automation becomes essential for maintaining visibility and control.
The economic argument for certificate lifecycle automation extends beyond preventing outages. ITIC found that over 90% of respondents estimated their cost of downtime to be over $300,000 per hour, standing true even for small and midsize organizations upto 200 employees.

ITIC states that if you’re a micro SMB with less than 25 employees and one server, your downtime might be an “extremely conservative” $1,670 per minute or about $100,000 an hour.
Core Components of Automated PKI Management
Discovery and Inventory Management
Comprehensive discovery forms the foundation of successful automation. By utilising discovery tools, organisations typically uncover more certificates than are tracked in spreadsheets. The visibility gap creates significant risk, as unmanaged certificates become potential failure points.
Automated discovery must encompass:
- Network scanning for TLS endpoints
- Cloud service integration (AWS, Azure, Google Cloud)
- Container and Kubernetes pod inspection
- Load balancer and CDN certificate identification
- IoT device certificate cataloging
Automated discovery and up-to-date inventory are prerequisites for reaching upper maturity levels (4 & 5) as emphasized by The PKI Consortium’s maturity model for modern certificate management.
Automated Renewal and Provisioning
The ACME protocol (RFC 8555) revolutionizes certificate provisioning by enabling automated validation that typically completes in a matter of seconds. This represents a dramatic reduction from the manual process, which can take hours to days per certificate or even 10 days to a month for complete renewal and installation.
Policy Engine and Governance
Effective automation requires robust policy enforcement. AppViewX’s policy engine enables organisations to define and enforce standards for:
- Key specifications: Minimum key lengths (2048-bit RSA, 256-bit ECC)
- Certificate attributes: SAN requirements, validity periods, signature algorithms
- Approval workflows: Risk-based routing for high-value certificates
- Compliance requirements: Industry standards (PCI DSS, HIPAA, SOC 2)
As cryptographic standards evolve, automation must also support crypto-agility. According to NIST and NSA guidance, organizations should begin preparing for post-quantum cryptography transitions before 2030, making policy-driven automation a critical capability.
Implementation Blueprint: Three-Phase Approach

Phase 1: Discovery and Assessment
Begin with comprehensive visibility using automated certificate discovery tools to identify all certificates across your infrastructure. The Enterprise Strategy Group research shows non-human identities outnumber human ones by 20:1, making thorough discovery essential.
Key activities:
- Deploy agentless scanning across network segments
- Integrate with cloud platforms and container orchestrators
- Document certificate ownership and dependencies
- Calculate baseline metrics for ROI measurement
- Identify high-risk certificates for priority automation
Phase 2: Transform Core Processes Through Smart Automation
Automate Critical Workflows
Replace manual renewal checks with automated workflows. With platforms like AppViewX AVX ONE, certificates renew automatically before expiration without human intervention for standard requests. As CA/Browser Forum Baseline Requirements evolve, automation ensures continuous compliance across the organization.
Implement Policy-Driven Management
- Instant policy-driven revocation with complete audit trails
- Dynamic compliance dashboards replacing manual data collection]
- Automated compliance reporting, reducing quarterly audit preparation from days to hours
Establish Governance Frameworks
Form a cross-functional Machine Identity Management Working Group to:
Phase 3: Achieve Enterprise-Scale Automation and Crypto-Agility
Native Platform Integration
Replace custom scripts with native Kubernetes integration, enabling certificate delivery at DevOps speed. Certificates are provisioned automatically into containerised applications without blocking deployment pipelines. Learn here how to streamline certificate management in Azure Kubernetes Service for cloud-native environments.
Enterprise System Orchestration
Integrate certificate lifecycle management with:
Build Crypto-Agility for the Future
The White House National Security Memorandum 10 (NSM-10) mandates that federal agencies complete their migration to post-quantum cryptography by 2035. When post-quantum algorithms require deployment, automated systems must identify affected certificates, generate replacements, and deploy across environments in hours rather than months. Review NIST’s crypto-agility strategies to prepare your organization for this transition.
TLS Certificate Management Software Comparison
When evaluating certificate lifecycle automation platforms, consider these critical capabilities:
Essential Features
- Multi-CA support: Support for multiple certificate authorities to avoid vendor lock-in
- Protocol flexibility: ACME, SCEP, EST, and proprietary APIs
- Cloud-native architecture: Scalability for millions of certificates
- Zero-touch renewal: Fully automated renewal without human intervention
- Comprehensive discovery: Agentless scanning across hybrid infrastructure
Integration Requirements
Modern certificate lifecycle automation must integrate seamlessly with your existing technology stack. AppViewX’s integration ecosystem includes:
- ITSM platforms: ServiceNow, BMC Remedy, Jira Service Management
- Cloud providers: AWS Certificate Manager, Azure Key Vault, Google Certificate Authority Service
- DevOps tools: Jenkins, GitLab, Terraform, Ansible
- Security platforms: Splunk, QRadar, CyberArk
According to Gartner’s latest research, organizations prioritizing integration capabilities achieve 50% faster implementation and 30% lower total cost of ownership.
Measuring Success: KPIs and Metrics
Operational Metrics
Track these key performance indicators to demonstrate automation value:
- Mean Time to Provision (MTTP): Target <5 minutes from request to deployment
- Certificate coverage: Aim for 95%+ automated management
- Renewal success rate: Should exceed 99.9% with proper automation
- Discovery accuracy: Track percentage of certificates under management
- Policy compliance: Monitor adherence to security standards
Business Impact Metrics
Quantify automation ROI through:
- Outage prevention: Number of potential outages avoided
- Cost avoidance: Calculate savings from prevented incidents
- Productivity gains: FTE hours redirected to strategic initiatives
- Audit performance: Reduction in compliance preparation time
- Security posture: Decrease in certificate-related vulnerabilities
Preparing for Future Requirements
Post-Quantum Readiness
The White House National Security Memorandum 10 mandates federal agencies complete migration to post-quantum cryptography by 2035, with an estimated cost of $7.1 billion. Organisations implementing automation now position themselves for seamless algorithm transitions when NIST’s post-quantum standards become mandatory.
Automation enables crypto-agility through:
- Centralized algorithm management
- Rapid certificate replacement capabilities
- Hybrid certificate support during transition
- Automated vulnerability scanning and remediation
Container and Kubernetes Automation
According to Red Hat’s 2024 State of Kubernetes Security report, a majority of organizations experienced at least one container or Kubernetes security incident in the last 12 months, with 45% reporting runtime incidents and 44% encountering issues in build and deployment phases. As teams scale their cloud-native environments, these numbers highlight the importance of eliminating manual, error-prone steps, including certificate provisioning and renewal.
This is where automated certificate management becomes critical. AppViewX streamlines this by providing native integration for:
- Ingress controller certificate management
- Service mesh TLS automation
- Pod-to-pod encryption
- Secrets rotation and management
Best Practices for Implementation Success
Start Small, Scale Fast
- Begin with high-risk certificates where automation delivers immediate value
- Pilot with 20-30% of portfolio to build confidence and refine processes
- Document lessons learned and adjust automation policies
- Scale to production once pilot demonstrates success
- Achieve full coverage within 6-12 months
Avoid Common Pitfalls
Organizations often struggle with:
- Incomplete discovery leading to shadow IT certificates
- Over-complex approval workflows that negate automation benefits
- Insufficient testing causing production failures
- Lack of executive sponsorship delaying implementation
- Treating automation as purely technical rather than business transformation
Build Organizational Capability
Successful automation requires cultural change:
- Train teams on automation tools and processes
- Establish clear ownership and accountability
- Create cross-functional working groups
- Document procedures and runbooks
- Celebrate automation wins to build momentum
The Path Forward: Taking Action
The transition to 47-day certificates isn’t a future consideration—it’s an immediate imperative. Organizations implementing certificate lifecycle automation now gain competitive advantages through operational efficiency, enhanced security, and infrastructure resilience.
Immediate Next Steps
- Assess your current state using the PKI Consortium’s maturity model
- Calculate your ROI potential based on certificate volume and outage history
- Evaluate automation platforms against your specific requirements
- Start discovery to understand your true certificate footprintBuild your business case with concrete metrics and timelines
- Build your business case with concrete metrics and timelines
Why AppViewX for Certificate Lifecycle Automation
AppViewX’s certificate lifecycle automation platform delivers:
- Comprehensive discovery across hybrid multi-cloud environments
- Policy-driven automation with zero-touch renewal
- Enterprise integrations with existing security and IT tools
- Crypto-agility for post-quantum readiness
- Proven ROI with customers achieving 70-90% reduction in management overhead across certificate lifecycle operations
Ready to transform your certificate management? Schedule a demo to see how AppViewX can automate your certificate lifecycle, or download our ROI calculator to quantify your automation opportunity
About AppViewX
AppViewX is a global leader in certificate lifecycle automation and machine identity management. Our platform enables enterprises to discover, manage, and automate certificates at scale across complex hybrid multi-cloud environments. With AppViewX, organizations achieve operational excellence while building crypto-agility for future security requirements.
Schedule Your Demo →

Uncategorized
Summary:
Use a Public CA when you need certificates for public-facing websites, customer applications, or any service accessed by external users, as public CAs are automatically trusted by all browsers and devices. Use a Private CA when securing internal networks, development environments, IoT devices, or any infrastructure where certificates only need to be trusted within your organization. Most enterprises need both: public CAs for external-facing services and private CAs for internal infrastructure, best managed through a unified certificate lifecycle management platform.
Consider weaving in CA-agnostic capabilities in the setup and conclusion as AppViewX is CA agnostic eliminating the threat of vendor locking.
Key Differences:
| Aspect |
Public CA |
Private CA |
| Best For |
Public websites, customer-facing apps, external APIs |
Internal networks, DevOps, IoT, employee authentication |
| Trust |
Automatic browser/device trust |
Manual trust deployment required |
| Cost Model |
Pay per certificate |
Setup cost + unlimited issuance |
| Certificate Transparency |
Required (public logs) |
Not required (privacy maintained) |
| Ideal Volume |
Low to medium volumes |
High volume needs (1000+ certificates) |
| Control |
Limited customization |
Full policy control |

Understanding Certificate Authorities (CAs): The Foundation of PKI
What is a Public Certificate Authority?
A Public Certificate Authority (CA) is a trusted third-party organization that issues SSL/TLS certificates for websites and applications accessible on the public internet. Public CAs are recognized and trusted by all major browsers and operating systems.
When you purchase an TLS certificate for your public-facing website, you’re obtaining it from a public CA that has been vetted and included in browser trust stores. These certificates enable the HTTPS connections users see when visiting secure websites.
What is a Private Certificate Authority?
Organizations often need to secure their internal infrastructure, applications, and users with digital certificates. When an organization establishes the capability to issue these certificates internally, it becomes a Private Certificate Authority. Private CA creates certificates that are only trusted within the organization’s own environment.
Which type of CA is right for your organization
The decision between Private CA and Public CA isn’t about choosing the “best” solution, it’s about matching your certificate infrastructure to your organization’s specific needs, scale, and growth trajectory. With the PKI market projected to reach USD 24.37 billion by 2032, growing at 20.1% annually, and Cloud/Managed PKI solutions expanding at 21.3% CAGR, you’re making this decision in a landscape where automation and scalability are no longer optional, they’re business necessities and competitive advantages.

Your path forward starts with understanding where certificates fit in your architecture today and where they need to take you tomorrow. Organizations currently manage thousands of internal certificates, yet still rely on spreadsheets for tracking. If that sounds familiar, you’re not behind, you’re at the perfect inflection point to build a certificate strategy that scales with your business rather than against it.
Public CA makes sense when you need immediate, universal trust. If your certificates protect customer-facing websites, e-commerce platforms, or services that external parties must validate, Public CA ensures trust through pre-installed root certificates in browsers and operating systems.
Private CA unlocks flexibility and scale for internal operations. When you’re securing internal applications, service-to-service communication, VPN access, or IoT device authentication, Private CA lets you define your own certificate policies, validity periods, and issuance workflows.
Automation for Public and Private CAs
The shift to automated certificate lifecycle management isn’t just about keeping pace with industry changes, it’s about positioning your organization to move faster and maintain digital trust. With recent CA/Browser Forum changes and a timeline that leads to 47-day certificate validity by March 2029 and machine identities growing 20 times faster than human identities, the organizations that automate today gain operational agility that compounds over time.
AVX ONE accelerates your automation journey. AppViewX helps companies manage their Certificate Authorities (CAs) by providing powerful certificate lifecycle management (CLM) solutions that automate, unify, and secure certificate operations across both public and private CAs in hybrid and multi-cloud environments. Rather than building custom integrations or managing multiple point solutions, it provides enterprise-grade certificate lifecycle automation that delivers results from day one.
The platform discovers certificates across your entire infrastructure regardless of issuer, automates end-to-end workflows from CSR (Certificate Signing Request) generation through deployment, and provides unified visibility across hybrid and multi-cloud environments.
Schedule Your Demo →

Uncategorized
For most organizations, Certificate Lifecycle Management (CLM) is still a tangled web of spreadsheets, manual request tickets, and last-minute fire drills when a certificate expires and takes down a critical production service. Every team, from DevOps to Marketing, needs certificates to keep their applications and services running, but getting a single certificate issued often means opening an ITSM ticket, waiting on approvals, and enduring several back-and-forth interactions.
This friction isn’t just an inconvenience, it’s a problem that traditional CLM tools, which often act as little more than expensive databases, have failed to solve.
And even when organizations invest in a CLM platform, implementations are rarely quick wins. Deployments can take months, bogged down by complex configurations, custom scripting, and heavy reliance on professional services.
The biggest bottleneck is policy definition. Every organization needs clear rules for how certificates are issued, renewed, and deployed across hybrid environments. But defining and enforcing those policies consistently has long been one of the hardest parts of CLM—until now.
Introducing the AppViewX Policy Engine.
Shift to an Automated Self-Service Model with AppViewX Policy Engine
The new AppViewX Policy Engine is built on self-service automation, making it the easiest and fastest way to automate policy workflows and deliver value from day one. It templatizes common CLM workflows into a library of ready-to-use “trust templates,” allowing teams to move from static, ticket-based processes to dynamic, automated policy enforcement—no scripting required.
For new customers, the impact is immediate: instead of spending months scripting and configuring workflows, teams can apply pre-built (or easily configured) policies on day one. This isn’t just a new feature; it’s a fundamental shift in how we approach certificate lifecycle management.
Highlights:
-
Automated Enrollment: Requesting a certificate no longer means filling out long forms or creating tickets. With Automated Enrollment, users simply submit the essential details through an intuitive self-service form. Approvers are automatically notified, and once approved, the system issues and delivers the certificate—no manual intervention, no delays, no friction.
Instead of brittle, step-by-step custom automation scripts, Policy Engine uses a declarative, “intent-based” model. You don’t build a complex, 20-step workflow for a single task, you define a policy.
For example, a “Web Server” certificate policy might specify:
“All web server certificates must be 2048-bit, valid for 1 year, sourced from this CA, and automatically re-enrolled with a new private key 30 days before expiration.”
Standard organization address and other details are auto-filled. The customer IT team only needs to specify the common name in a self-service form. From there, the system automatically generates the certificate, routes it through the necessary approvals, and delivers it to the requester—no manual steps, no back-and-forth.
You are no longer building a process. You are defining a rule. The “how” becomes automated, consistent, and most importantly, auditable, while removing bottlenecks and freeing up resources for the Network and PKI teams that manage the CLM process.
-
Policy-Driven Re-enrolment (with New Key Generation): This is critical. A simple renewal that reuses the same private key isn’t real security; it’s a risk disguised as convenience. The Policy Engine enforces best practices automatically, ensuring every certificate renewal generates a new key pair. This ensures cryptographic hygiene, reducing the risk of key compromise.
- Automated Device Onboarding: For network teams managing hybrid and cloud-native environments, this is the game-changer. New devices can be securely and automatically onboarded to enable better certificate discovery and provisioning through last-mile automation.
 Ready-to-use templates for common CLM actions
Ready-to-use templates for common CLM actions
The Policy Engine Advantage
-
Faster Time-to-Value: Pre-built templates and automated workflows get teams up and running immediately, reducing deployment and configuration time from months to days or hours.
-
Self-Service Simplicity: Empowers teams to request and issue certificates on their own, without waiting for support from the IT team, reducing bottlenecks and accelerating operations.
-
Configurable for All Environments: Flexibility to tailor policies to meet the needs of hybrid, multi-cloud, or complex enterprise setups while maintaining consistency and compliance.
-
Easier Renewals: Automated certificate re-enrollment ensures seamless, friction-free renewals, reducing risk and administrative overhead.
-
Supports Every Use Case: Whether your goal is quick wins with ready-to-use templates or advanced, policy-driven automation, Policy Engine scales to meet your requirements.
Core Capabilities of Policy Engine
| Feature |
What It Delivers |
Why It Matters |
| Predefined Policies |
Out-of-the-box configurations for the most common CLM use cases. |
Enables rapid, self-service onboarding with zero friction. |
| Admin Configurable Templates |
Define enrollment behavior and self-service UI for delegated access. |
Meets growing certificate demands across teams while maintaining control and consistency. |
| Central Policy Governance |
Unified policy management across all certificate groups. |
Ensures consistency, compliance, and repeatability across teams and business units. |
How Can I Get This?
Policy Engine is automatically available for all on-prem and SaaS AVX ONE CLM customers as part of AppViewX’s November 2025 release. With Policy Engine, AppViewX customers can deploy CLM at the speed of business, accelerating automation, improving compliance, and freeing IT and security teams to focus on innovation rather than configuration.
If you are new to AppViewX, then contact us to see how Policy Engine can eliminate manual chaos and bring order, consistency, and speed to every stage of certificate lifecycle management.
Frequently Asked Questions (FAQs)
-
What is AppViewX Policy Engine and how does it help with CLM?
AppViewX Policy Engine is a self-service, policy-driven automation framework within AVX ONE CLM. It simplifies certificate issuance, renewal, and governance by replacing manual processes with automated, auditable workflows, reducing friction, errors, and operational overhead.
-
How quickly can organizations deploy CLM using Policy Engine?
With pre-built policy templates for common certificate workflows, organizations can deploy CLM in hours / days instead of months. With pre-built templates for common certificate workflows, teams can get started immediately, while still having access to advanced visual workflow customization for complex environments.
-
How does Policy Engine simplify certificate requests and approvals?
Policy Engine introduces self-service enrollment with pre-defined forms that capture only essential details. Once submitted, requests automatically route through approval workflows and deliver certificates, eliminating the need for tickets, manual steps, or back-and-forth communication.
-
How can automation simplify certificate deployment to servers and devices?
Automation allows certificates to be securely pushed to endpoints with preconfigured key formats and restart settings, minimizing downtime and ensuring trust consistency across the network.

Uncategorized
As enterprises face growing pressure to secure machine identities, the landscape is shifting rapidly. The post-quantum era is approaching, with NIST’s impending cryptography standards forcing organizations to rethink how they safeguard digital assets. At the same time, the CA/B Forum’s new 47-day certificate mandates will dramatically shorten certificate lifecycles, exposing the limits of manual management. These shifts, coupled with the general increase in digital assets and expanding attack surface, are creating significant pain points for security and IT teams.
With our November 2025 release, AppViewX delivers a major leap forward. We are helping customers prepare for the future by accelerating deployment, automating compliance, and reducing operational overhead across every part of certificate lifecycle management (CLM).
This release introduces four innovations designed to help teams work faster, smarter, and more securely:
-
Manage Short-Lived Certificates at Scale: Meet the 47-day mandate by automating certificate renewal cycles and enforcing re-enrollment policies without added overhead.
-
Accelerate Post-Quantum Cryptography (PQC) Readiness with Quantum Trust Hub: Assess your crypto-agility across source code, apps, certificates, databases, containers, and more with a complete Cryptographic Bill of Materials (CBOM) and remediation recommendations.
-
Improve User Experience with AppViewX InfinityAI: Rapidly navigate to the data you need, generate reports with natural language queries and accelerate onboarding through AI-based navigation.
-
Achieve Faster Time-to-Value with Policy Engine: Deploy CLM in days—not months—with out-of-the-box policy templates, while retaining the flexibility to customize workflows for complex environments.
Together, these features empower Security, DevOps, and IT teams to reduce manual effort, increase compliance, and get ahead of the industry’s most pressing changes.
Short-Lived Certificate Management: Automate Compliance, Eliminate Risk
The CA/B Forum’s upcoming 47-day certificate lifecycle mandate will increase renewal frequency by up to eight times by 2029, with the first phase of reduced certificate validity (200 days) starting in March 2026. The new Short-Lived Certificate Management capabilities in AVX ONE are purpose-built to automate compliance and eliminate overhead.
Capabilities include:
-
Automated Onboarding and Discovery: Instantly detect and onboard endpoints (servers, network devices, IoT, etc.) for streamlined certificate provisioning.
-
Automated Domain Control Validation (DCV): Meet 47-day compliance by validating domains and issuing renewals automatically—no manual effort required.
-
Certificate Lifecycle and Validity Enhancements: Define new certificate validity for renewals, generate new private keys, and use templated re-enrollment policies for consistent compliance.
By automating discovery, validation, and renewal, organizations can mitigate outages, reduce human error, and maintain compliance with shorter certificate validity timelines with minimal overhead.
Key benefits:
- Continuous compliance with CA/Browser Forum mandates.
- Fewer outages, security breaches, and compliance gaps.
- Reduced operational overhead through automation and visibility.
See how to automate 47-day certificate compliance →
Quantum Trust Hub: Prepare for the Post Quantum Cryptography Era
The rise of quantum computing presents an existential challenge to today’s encryption standards. With NIST’s release of post-quantum cryptography (PQC) algorithms, security leaders are now under pressure to assess and plan their migration to quantum-safe cryptography before it’s too late.
The new Quantum Trust Hub helps organizations assess, prioritize, and plan their migration to quantum-safe encryption.
Capabilities include:
-
Enterprise Assessment & Remediation: Get a comprehensive assessment of certificates, algorithms, protocols, libraries, and keys—complete with a Cryptographic Bill of Materials (CBOM) and remediation recommendations.
-
Comprehensive Reporting: Generate a full-featured report that assesses your crypto-agility across source code, apps, certificates, databases, containers, and more.
-
Dashboard Insights: Consolidate data and insights into one view, enabling leadership to make informed, strategic decisions on crypto posture across the organization.
With a unified view of cryptographic assets and vulnerabilities, teams can confidently plan and prioritize their path to quantum-safe encryption.
Key benefits:
- Understand your crypto-readiness instantly with clear vulnerability counts and remediation guidance.
- Adapt to new standards published by NIST, NCSC, and other regulatory agencies.
- Demonstrate security leadership and meet compliance requirements.
Learn more about assessing your PQC readiness →
InfinityAI: Reduce Operational Costs with AI-Enabled Search and Navigation
As platforms grow more powerful, they also require greater expertise to navigate. Finding data or building reports often takes time and requires help from support teams. InfinityAI changes that experience. Integrated across help, search, navigation, and reporting, it allows users to ask for what they need in plain language—whether it’s building a report, finding a configuration page, or troubleshooting an issue.
Capabilities include:
-
AI-Enabled Navigation: Allows users to navigate by simply stating what they need to do, for example “rotate a certificate” or “add a new device group”.
-
Natural Language Search and Reporting: Quickly search or build custom reports by using AI-enabled prompts.
-
Intelligent Knowledge Base: Find answers to product-related questions using a simple, conversational
interface.
The outcome is a more intelligent user experience that turns complex operations into effortless actions.
Key benefits:
- Context-aware guidance reduces onboarding, learning curves and improves user experience.
-
Any user can now self-serve insights without relying on internal support teams, increasing overall efficiency.
- A common AI interface that extends across the AVX ONE SaaS platform.
Discover how InfinityAI transforms CLM operations →
Policy Engine: Faster Time to Value, No Complexity
Getting value from a CLM platform shouldn’t take months. Yet traditional systems often require extensive configuration and a service engagement before teams see results.
With the new Policy Engine, AVX ONE delivers an out-of-the-box onboarding experience that dramatically accelerates time to value. Customers can now use predefined policies that cover the most common CLM use cases, as well as customize policies and workflows for more complex configurations.
Capabilities include:
-
Pre-defined policy templates: Leverage templates for common use cases to onboard faster while retaining the option to use visual workflows for more complex custom use cases.
-
Automated device onboarding: Detect and onboard devices automatically, enabling faster discovery and provisioning of certificates.
-
Admin configurable template options: Define enrollment behavior and UI for delegated access to meet increased certificate needs across teams.
This flexibility reduces deployment and configuration time from months to days.
Key benefits:
- Faster time to value through simplified, self-service deployment.
- Streamlined certificate re-enrollment minimizes friction during renewal processes.
- Flexibility to tailor policies for unique enterprise environments.
Learn more about Policy Engine →
Delivering Continuous Innovation
The AVX ONE November 2025 release delivers a major leap forward in helping customers future-proof their machine identity ecosystems while dramatically simplifying deployment, operations, and user experience. This release introduces faster implementation, intelligent automation, instant certificate discoverability, and built-in compliance enforcement—all powered by PQC-ready cryptography and guided workflows that reduce complexity and risk.
By unifying speed, security, and simplicity into a single platform experience, AppViewX is enabling customers to stay ahead of emerging threats, adapt to evolving standards, and scale trust across every machine identity.
The release is now available. Find full release notes and resources on the Product Release Hub or contact your customer success team for questions. You can also download Product datasheet to learn more.
Frequently Asked Questions
-
Does the Certificate Lifecycle Management automation support both public and private CAs?
Yes. AVX ONE supports all major public and private CAs and can automate renewals across hybrid environments.
-
How do I get InfinityAI?
InfinityAI can be turned on by your Admin if you are a SaaS-delivered CLM customer. Permissions to access the feature are defined by role.
-
Does InfinityAI store / send customer data outside of the AVX ONE platform?
No. Customer specific data is not sent outside of the platform or provided as an input to external LLMs.

Uncategorized
Summary:
Enterprise-class Certificate Lifecycle Management (CLM) software must provide these features at a minimum: continuous discovery to scan all environments, central repository for unified certificate inventory, automated enrollment and renewal via ACME protocol, policy enforcement for cryptographic standards, continuous monitoring with predictive alerts, automated rotation before expiration, and reporting dashboards for compliance metrics.
Certificate lifecycle management software provides the automated control organizations need for comprehensive certificate and PKI ecosystem management.
Table Stakes Capabilities for Enterprise CLM Software
To effectively manage digital certificates at enterprise scale, your CLM solution must deliver specific core capabilities. These foundational features separate basic certificate tracking from comprehensive lifecycle automation.
The table below outlines the critical capabilities every enterprise CLM platform should provide, along with why each matters and how it performs in practice.
| Capability |
Critical Importance |
Performance Requirements |
| Continuous Discovery |
Eliminates blind spots across multi-cloud environments |
Automated, agent-less certificate discovery with continuous scanning and intelligent tagging for renewal workflows |
| Centralized Repository |
Essential for visibility and governance |
Unified certificate inventory consolidating metadata, cryptographic algorithms, and expiration tracking |
| Automated Enrollment |
Reduces manual CA requests |
Integration with ACME protocol for automated certificate issuance and renewal workflows |
| Policy Enforcement |
Ensures consistency and compliance |
Framework for approved CA usage and lifecycle governance with automated policy validation |
| Continuous Monitoring |
Enables proactive management |
Predictive alerting system tracking certificate status across all lifecycle stages |
| Automated Renewal |
Minimizes manual intervention |
Systematic renewal workflows triggered before expiration with zero-touch rotation capability |
| Reporting Dashboard |
Provides compliance visibility |
Analytics dashboards tracking KPIs like crypto resilience scorecards for audit readiness |
Manual Processes vs. CLM Automation
The gap between traditional manual certificate management and modern CLM automation is substantial.
Organizations still relying on spreadsheets, manual tracking, and fragmented processes face significantly higher operational costs, security risks, and outage frequency.
This comparison illustrates how automation transforms each critical stage of certificate management.
| Process Stage |
Traditional Management |
CLM Automation |
| Discovery |
Manual spreadsheet audits |
Continuous agent-less monitoring across all environments |
| Renewal Tracking |
Inefficient manual checks |
Automated notification alerts with zero-touch renewal workflows |
| Revocation Management |
Error-prone with delayed response |
Instant policy-driven revocation with complete audit log visibility |
| Compliance Reporting |
Time-intensive manual data collection |
Dynamic dashboards with automated compliance-ready reporting |
| Kubernetes Integration |
Custom scripts with manual dependencies |
Native integration enabling certificate delivery at DevOps speed |
| Crypto Agility |
Reactive certificate replacement |
Proactive policy-driven cryptographic transitions ensuring compliance |
How AppViewX AVX ONE Leads the CLM Industry
AppViewX AVX ONE represents the next generation of certificate lifecycle management, delivering comprehensive automation and intelligence that traditional approaches cannot match.
Here’s how AVX ONE compares to conventional CLM platforms.
| Capability |
Traditional CLM |
AppViewX AVX ONE |
| Discovery |
Often manual with incomplete visibility |
100% automated continuous discovery across all environments including containerized systems |
| Policy Enforcement |
Manual, error-prone processes |
Real-time policy enforcement with automated violation alerts |
| Renewal & Rotation |
Scheduled renewals vulnerable to lapses |
Intelligent incident-driven automation preventing outages |
| Compliance Reporting |
Static, outdated templates |
Dynamic crypto resilience scorecard with audit-ready dashboards |
| Machine Identity Security |
Primarily TLS-focused |
Comprehensive protection for all machine identities with automated threat detection |
| Scalability |
Static, limited architecture |
Flexible design supporting millions of certificates across hybrid and multi-cloud environments |
Outlook: The 47-Day SSL/TLS Reality
The progressive reduction in SSL/TLS certificate validity represents a fundamental shift in digital trust management. Organizations must prioritize proactive automation and unified certificate governance to avoid certificate outages.
Ready to strengthen your digital trust? Let our experts demonstrate how AppViewX AVX ONE automates and fortifies your certificate lifecycle processes.
Optimal CLM Strategy
Effective certificate management demands rigorous compliance practices. Key elements include:
- Unified Certificate Inventory: Maintain a structured repository tracking certificate quantities, locations, and expiration dates.
- Proactive Renewal Systems: Implement automated alerts and renewal workflows to prevent expiration-related outages.
- Strong Cryptography: Enforce consistent cryptographic policies to eliminate configuration vulnerabilities.
- Secure Key Storage: Protect private keys in hardened repositories, misconfigured keys pose severe enterprise risks.
Future Trends & Final Thoughts
The CA/Browser forum’s mandate reducing TLS certificate lifetime from 398 days to 47 days by 2029 fundamentally changes operational requirements. This dramatically increases renewal workload, demanding that CLM solutions provide:
Certificate Visibility
In a 47-day TLS environment, enhanced certificate visibility directly correlates with scalability and operational resilience.
Enhanced Automation
Shortened lifecycles require automated systems that ensure consistent, rapid renewals with minimal error rates.
Ongoing Policy Control
Frequent renewals demand robust control systems preventing accountability gaps and ensuring continuous policy enforcement.
Critical Takeaway: Without proper visibility, organizations will fail to renew critical certificates. Comprehensive automation is essential, not just for managing end-to-end certificate processes, but for eliminating operational inefficiencies in certificate management.
Contact us to explore AVX ONE’s advanced certificate lifecycle management capabilities in detail.
Schedule Your Demo →

Uncategorized
Summary:
- Reduce SSL outages by: (1) Discovering and cataloging all certificates across your entire infrastructure automatically (2) Implementing automated certificate renewal and provisioning to eliminate manual errors, (3) Setting up multi-stage expiration alerts and automated workflows, and (4) Maintaining complete certificate inventory visibility through automated discovery tools. Organizations using certificate lifecycle management platforms like AppViewX to eliminate certificate-related downtime completely.
- SSL outages are a preventable problem. Organizations that implement automated certificate lifecycle management to eliminate outage incidents like PacificSource did in their recently publicized automation initiative.
- Enterprises should implement complete certificate visibility, continuous monitoring and automated policy-based renewals.
- With certificate lifespans decreasing to 47 days by 2029 (CA/Browser Forum Ballot SC-081v3), enterprises managing thousands of certificates across hybrid environments face an impossible task. Manual tracking inevitably leads to missed expirations that trigger outages in critical applications and APIs, often at the worst possible moment.
Considering it takes at least 5 hours to remediate a certificate-related outage, reduction in the incident numbers of outages should be a top priority for any enterprise.
In this guide, we’ll dive into the root causes of SSL or TLS certificate outages, proven strategies to prevent expiration-related downtime, best practices for automated monitoring and renewal, and how to build a resilient certificate management system that scales with your infrastructure.
What are SSL outages and why do they matter?
An SSL or TLS certificate outage occurs when a digital certificate fails, preventing secure encrypted connections between users and your applications. When certificates expire, are misconfigured, or become invalid, browsers display security warnings, APIs reject connections, and critical services become inaccessible and damage trust.
What users may experience:
- Red warning screens stating “Your connection is not private”
- Blocked access to websites and applications
- Failed API calls and broken integrations
- Crashed mobile app

Common triggers include:
- Expired certificates, leading cause of certificate-related outages, accounting for 81% of outages organizations in the past year
- Installation errors, including misconfigured certificates or incorrect server settings
- Domain mismatches in which the certificate doesn’t match the domain name being accessed
- Broken certificate chains with missing or incorrect intermediate certificates
- Certificate revocations due to compromised or invalidated certificates
How can you prevent SSL certificate expiration?
It is important to understand why manual certificate tracking fails at scale for enterprises. There was once a time when certificates had a 3 year expiration date. In those days, it was feasible to do manual certificate tracking and renewals.
However, as organizations manage thousands of certificates and certificate visibility remains low (up to 64% of organizations are unaware of the number of certificates deployed), enterprises are not ready for the upcoming 47-day expiration mandate. Manual tracking and remediation is a challenge now and will become unfeasible in the next year, becoming a recipe for outages and lost revenue.
Implementing automated certificate renewal and provisioning
Certificate lifecycle automation eliminates manual bottlenecks that cause outages. Modern platforms monitor expiration dates and trigger renewal workflows at configurable thresholds (30/60/90 days), then automatically:
- Reuse existing keys or generate certificate signing requests (CSRs)
- Submit to the appropriate Certificate Authority
- Validate domain ownership
- Retrieve and deploy issued certificates
- Verify installation and log all actions
Key automation capabilities:
ACME Protocol Integration: The Automated Certificate Management Environment (ACME) protocol enables zero-touch certificate issuance, automated domain validation, and seamless integration with Let’s Encrypt and commercial CAs.
Multi-CA Support: Enterprise solutions integrate with multiple Certificate Authorities, both public and private PKI, allowing flexible CA routing and migration without service disruption.
Self-Service Provisioning: DevOps and application teams can request certificates via self-service portals or APIs while security maintains policy control, reducing IT bottlenecks and ensuring compliance.
The impact: Organizations implementing automation reduce manual certificate work by up to 90% and cut certificate-related downtime from 20-30 hours per year to under 2 hours.

How does AppViewX eliminate certificate blind spots?
AppViewX is a comprehensive certificate lifecycle management platform designed to eliminate the visibility gaps and manual processes that cause outages.
Complete infrastructure discovery:
AVX ONE automatically discovers certificates across 100+ platforms and technologies, including:
- Public and private cloud environments (AWS, Azure, GCP)
- Load balancers (F5, Citrix ADC, A10, Kemp
- Web servers and application servers
- Kubernetes and container orchestration platforms
- API gateways and service meshes
Unlike point solutions that require agents or complex integrations, AppViewX uses agentless discovery to provide immediate visibility without infrastructure changes.
| Challenge |
How AppViewX Solves It |
Business Impact |
| Certificate blind spots |
Automated discovery across 100+ platforms with centralized dashboard |
Complete visibility into certificate inventory |
| Manual renewal processes |
Automated policy-based workflows with multi-stage alerts (30/60/90 days) |
97% reduction in manual certificate tasks |
| Certificate-related outages |
Zero-touch renewals and automated deployment and application binding |
Elimination of certificate outages |
| CA vendor lock-in |
Multi-CA orchestration (public + private PKI) |
Vendor flexibility and seamless migration |
| DevOps bottlenecks |
Self-service portal with policy enforcement |
Faster certificate deployments without compromising security |
| Future cryptographic changes |
Bulk replacement and algorithm migration capabilities |
Ready for 47-day lifespans and post-quantum cryptography |
Stop certificate outages before they blindside you
Don’t wait for the next $5,600-per-minute outage or 47-day certificate lifespan mandates to realize your certificate management needs automation.
See how AppViewX helps enterprises:
- Eliminate certificate-related outages
- Reduce manual certificate work by 97%
- Gain complete visibility across 100+ platforms
- Automate renewals with zero-touch workflows
- Prepare for post-quantum cryptography
Get a personalized demo and see how AppViewX can transform your certificate operations from reactive firefighting to proactive automation.
Schedule Your Demo →
Frequently asked questions (FAQs):
What causes most SSL certificate outages?
Expired certificates cause the majority of SSL outages, with most organizations experiencing at least one certificate-related outage in the past year. Other common causes include misconfigured certificates during installation, domain name mismatches, broken certificate chains, and lack of visibility into certificate inventory.
Can SSL certificate management be automated?
Yes, SSL certificate management can and must be automated, especially as certificate lifespans shrink to 47-day intervals by 2029 and exponentially increase the workload associated with monitoring and managing them. Certificate lifecycle management automation platforms do the heavy lifting of keeping an always current inventory of certificates, flagging pending expirations, automating renewals, provisioning, and monitoring across an entire IT infrastructure.

Uncategorized
Join Tom Herrmann and Joosua Danson for a practical, experience-driven session on how automation can streamline key patient-access workflows by reducing manual work and improving operational accuracy.
This webinar is designed for US healthcare organizations looking for real-world examples of how automation can support staff, reduce administrative burden, and improve the flow of patient-access tasks across high-volume departments.
The post Live Webinar: The Next Evolution in Patient Access: AI & Automation appeared first on Digital Workforce.



















 Ready-to-use templates for common CLM actions
Ready-to-use templates for common CLM actions




